Your Mobile Apps Are the New Front Door
Most security tools are blind to the unique risks in mobile applications. SafeNodeLabs gives you complete visibility, embedding security into your development lifecycle to protect your most critical user endpoint.
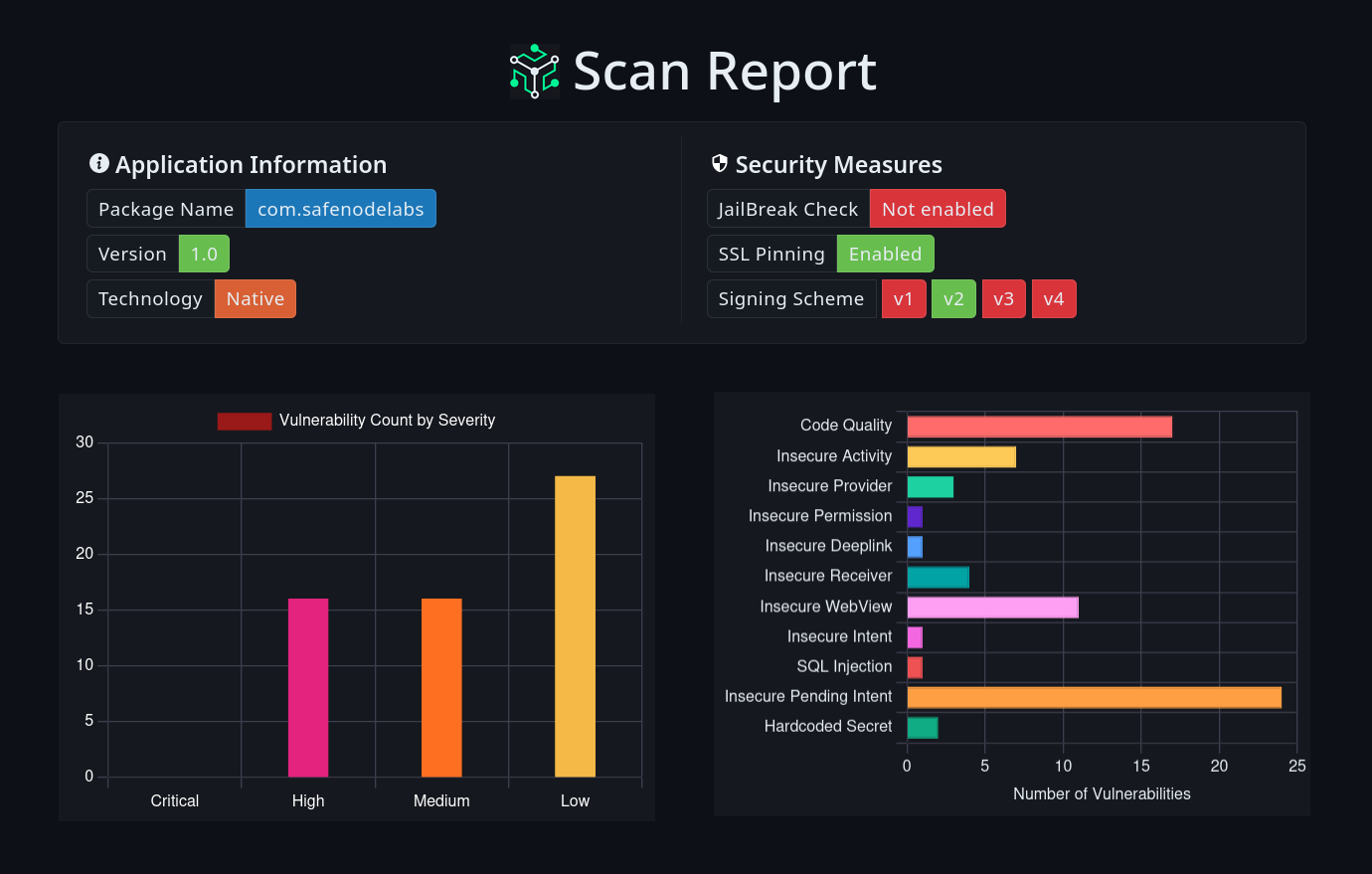
Find Vulnerabilities in Minutes
Don't wait days for a security review. Our CI/CD integrations find flaws in minutes, providing fast feedback where developers work and eliminating security as a bottleneck.
Consolidate Your Security Stack
One dashboard to rule them all. Unify SAST, DAST, SCA, and privacy scanning results for a complete, real-time view of risk across your entire mobile app landscape.
Translate Security to Business Value
Protect your revenue and reputation. Proactively fix issues that lead to data breaches, compliance fines, and loss of user trust with quantifiable risk metrics.
Don't Let Your App Be a Liability
Mobile vulnerabilities have real-world consequences. Proactively securing your apps is essential for protecting your users, your data, and your bottom line.
Built for Every Stakeholder
SafeNodeLabs empowers every role in the software development lifecycle, creating a unified security front from code to cloud.
Actionable Insights, Right in Your Workflow
Empower developers to code securely without slowing them down. Our tool provides clear, context-rich feedback directly where they work.
- Get remediation advice in your Pull Requests.
- Fix vulnerabilities with code-level guidance.
- Less context switching, more secure coding.
Govern and Triage from a Single Dashboard
Gain a unified view of risk across your entire mobile portfolio. Enforce security policies and prioritize what matters most.
- Manage risk with application-level context.
- Generate compliance reports effortlessly.
- Triage and assign vulnerabilities from one place.
Automate Security Gates in Your Pipeline
Shift security left by embedding automated scanning directly into your CI/CD pipelines. Ship fast without sacrificing security.
- Upcoming Fail builds based on custom, risk-based policies.
- Upcoming Automate scans on every commit or build.
- Upcoming Integrate with Jenkins, GitLab, GitHub Actions & more.
From Manual Drudgery to Strategic Impact
SafeNodeLabs acts as a force multiplier for your security team, automating the routine to free up your experts for the threats that matter most.
Manual Security Review
- Manually hunting for OWASP Top 10 flaws.
- Wasting hours chasing false positives.
- Lacking context for effective prioritization.
- Limited time for deep, exploratory testing.
Pentesting with SafeNodeLabs
- Automated: OWASP Top 10 & beyond found in minutes.
- Deep Context: Instantly trace data flow from source to sink to validate findings faster.
- Reproducible: Generate Proof-of-Concept exploits to confirm and fix vulnerabilities.
- Empowered: Experts focus on high-impact business logic flaws.
Find & Fix Flaws Faster, For Less
Integrating security into the CI/CD pipeline doesn't just reduce risk—it dramatically cuts remediation time and costs, boosting developer productivity.
Automated vs. Manual: The Financial Choice
The cost to fix a security vulnerability skyrockets the later it's found. Our automated SAST tool empowers developers to fix flaws instantly, a process that is drastically cheaper than finding them later via expensive manual penetration tests or after a costly production breach.
- Dramatically reduce the cost of remediation.
- Increase developer velocity by keeping them in their workflow.
- Ship more secure features, faster.
Relative Cost to Remediate a Vulnerability
Go From Noise to Actionable Insight
Our three-step process transforms raw scan data into clear, developer-ready remediation tasks, giving security managers unprecedented visibility and control.
Connect & Scan
Integrate with your CI/CD pipeline or upload your APK/AAB. Our engine performs a deep analysis of your code and its dependencies in minutes, not days.
Visualize the Full Attack Path
We don't just show you a vulnerability; we show you how it can be exploited. Our reports map the complete source-to-sink data flow, giving you the context needed to prioritize effectively.
Remediate with Precision
Every finding comes with a reproducible Proof-of-Concept exploit and actionable, code-level recommendations. Empower your developers to fix vulnerabilities correctly the first time.
One Platform, Total Visibility
Our interconnected scanning engine provides a complete, 360-degree view of your application's security health.
Static Analysis (SAST)
Find code-level vulnerabilities and security hotspots before a single line is compiled.
Dynamic Analysis (DAST)
Analyze your app's runtime behavior in a secure sandbox to uncover hidden, dynamic threats.
Dependency Scanning (SCA)
Identify known vulnerabilities (CVEs) in your open-source libraries and third-party dependencies.
Privacy Analysis
Detect data leaks and ensure your application complies with GDPR, CCPA, and other regulations.
Malware Detection
Scan for trojans, spyware, and other malicious code using our extensive threat intelligence database.
Compliance Reporting
Generate automated reports for PCI-DSS, HIPAA, and other standards to simplify your audit process.
Comprehensive Coverage for Modern Mobile Threats
Our scanning engine is built to find the most critical security flaws, including the complete OWASP Mobile Top 10, ensuring you have the coverage needed to meet enterprise compliance and security standards.
- M1: Improper Platform Usage
- M2: Insecure Data Storage
- M3: Insecure Communication
- M4: Insecure Authentication
- M5: Insufficient Cryptography
- M6: Insecure Authorization
- M7: Client Code Quality
- M8: Code Tampering
- M9: Reverse Engineering
- M10: Extraneous Functionality
Trusted by the Teams Building What's Next
From fast-growing startups to Fortune 500 companies, see why the best mobile teams choose SafeNodeLabs.
"SafeNodeLabs is the bedrock of our AppSec program. The ability to automate scans in CI and get actionable results in Jira has fundamentally changed how our developers and security teams collaborate. We're not just finding bugs; we're building a culture of security."
"As a developer, the last thing I want is security that slows me down. SafeNodeLabs is the opposite. It gives feedback in my pull requests, it's fast, and the remediation advice is actually useful. It's security that empowers, not blocks."
"User trust is our most valuable asset. SafeNodeLabs allows us to build security into the product from day one, which is a huge competitive advantage. It helps us protect our users and our brand reputation without slowing down our release schedule."
Integrate, Don't Interrupt
SafeNodeLabs plugs directly into the tools your team already loves. Enhance your workflow, don't replace it.
Secure Your Mobile Future
Find out why leading enterprises trust SafeNodeLabs to protect their most critical mobile applications. Get started in minutes.
Start Your Free ScanTransparent Pricing for Every Team
Choose the plan that fits your needs. Start scanning in minutes and scale as you grow.
Starter
For individuals and small teams getting started with AppSec.
- 10 Scans / month
- Static Analysis (SAST)
- Dependency Scanning (SCA)
- Email Support
Professional
For growing teams that need to integrate security into their workflow.
- 50 Scans / month
- SAST, DAST & SCA
- CI/CD Integrations
- Jira & Slack Integration
- Priority Support
Enterprise
For large organizations with advanced security and compliance needs.
- Unlimited Scans
- All Professional Features
- Advanced Compliance Reporting
- Dedicated Account Manager
- 99.9% Uptime SLA
See SafeNodeLabs in Action
Schedule a personalized, no-pressure demo with one of our AppSec specialists. We'll show you how you can integrate automated security into your workflow in under 30 minutes.
We've pre-configured the widget to match the site's dark theme. You can further customize colors in your Calendly account settings.